Description
The more you install themes and plugins, the more likely your sites will be vulnerable, even if you securely harden your sites.
While WordPress.org provides excellent resources, themes and plugins may often get vulnerable due to developers’ human factors such as lack of security awareness, misuse and disuse of the best practices in those resources.
This plugin focuses on insights into such developers’ human factors instead of detecting the specific attack vectors after they were disclosed. This brings a smart and powerful methods named as “WP Zero-day Exploit Prevention” and “WP Metadata Exploit Protection“.
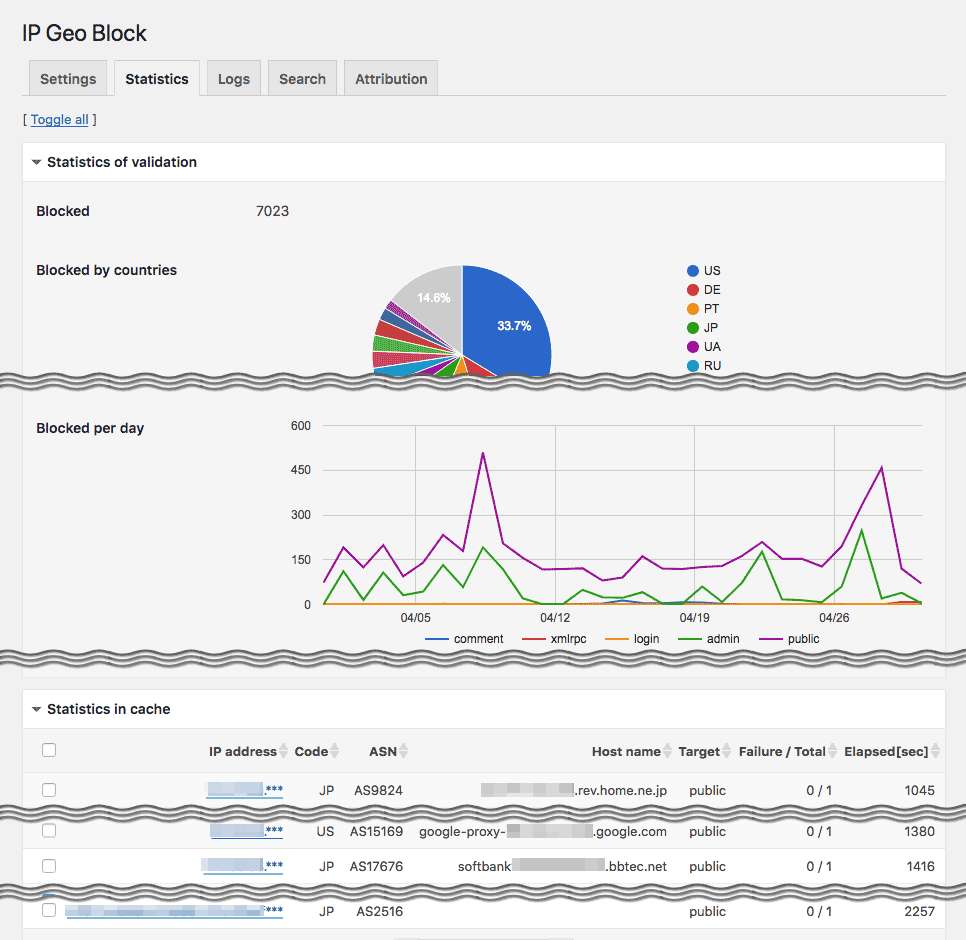
Combined with those methods and IP address geolocation, you’ll be surprised to find a bunch of malicious or undesirable access blocked in the logs of this plugin after several days of installation.
Features
-
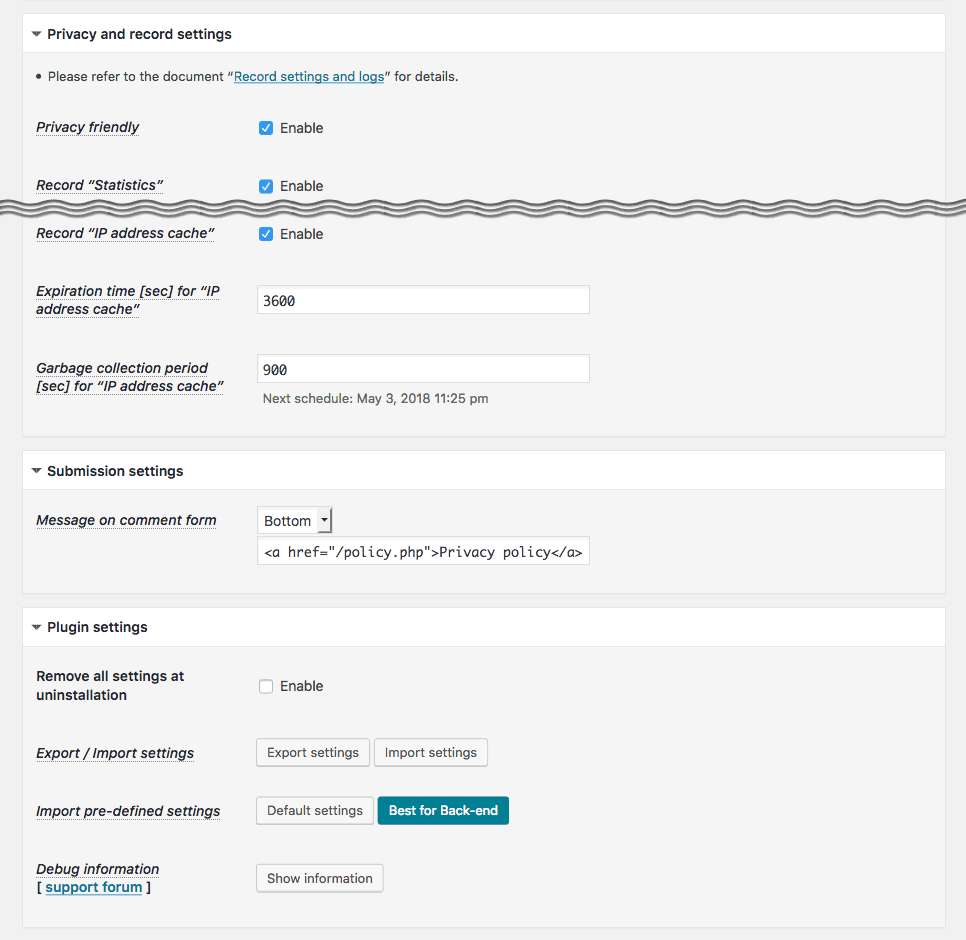
Privacy by design:
IP address is always encrypted on recording in logs/cache. Moreover, it can be anonymized and restricted on sending to the 3rd parties such as geolocation APIs or whois service. -
Immigration control:
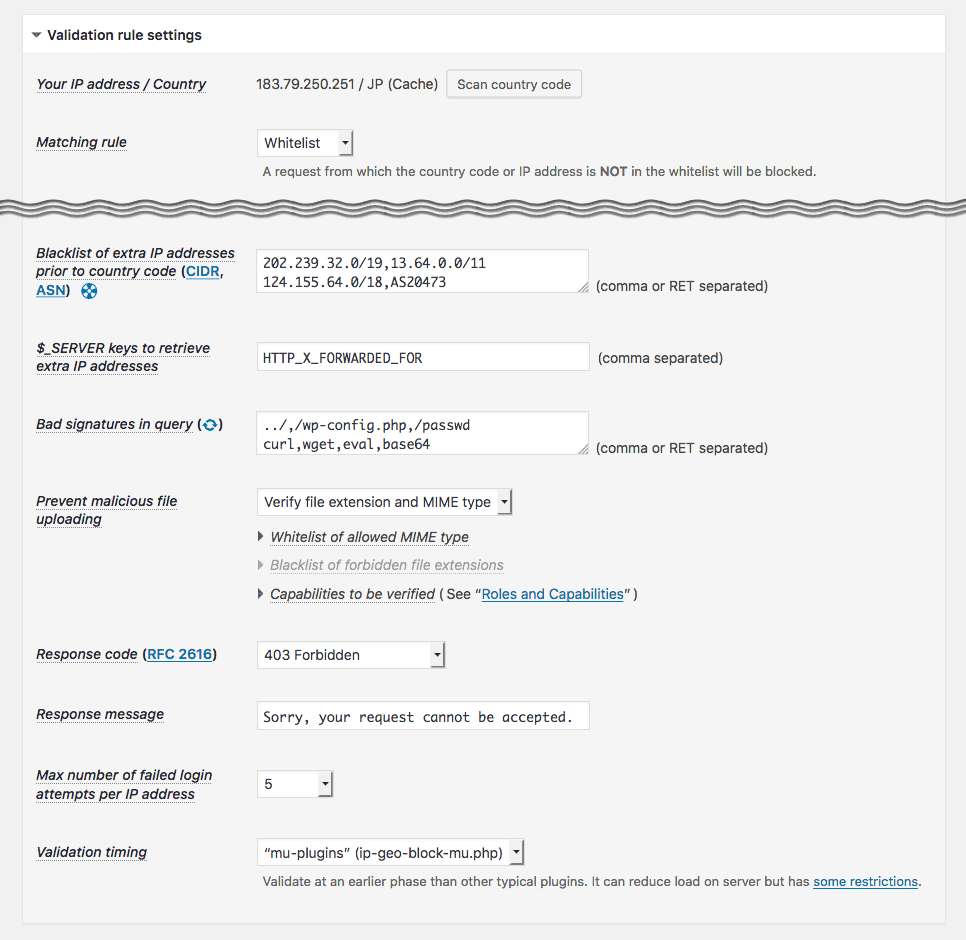
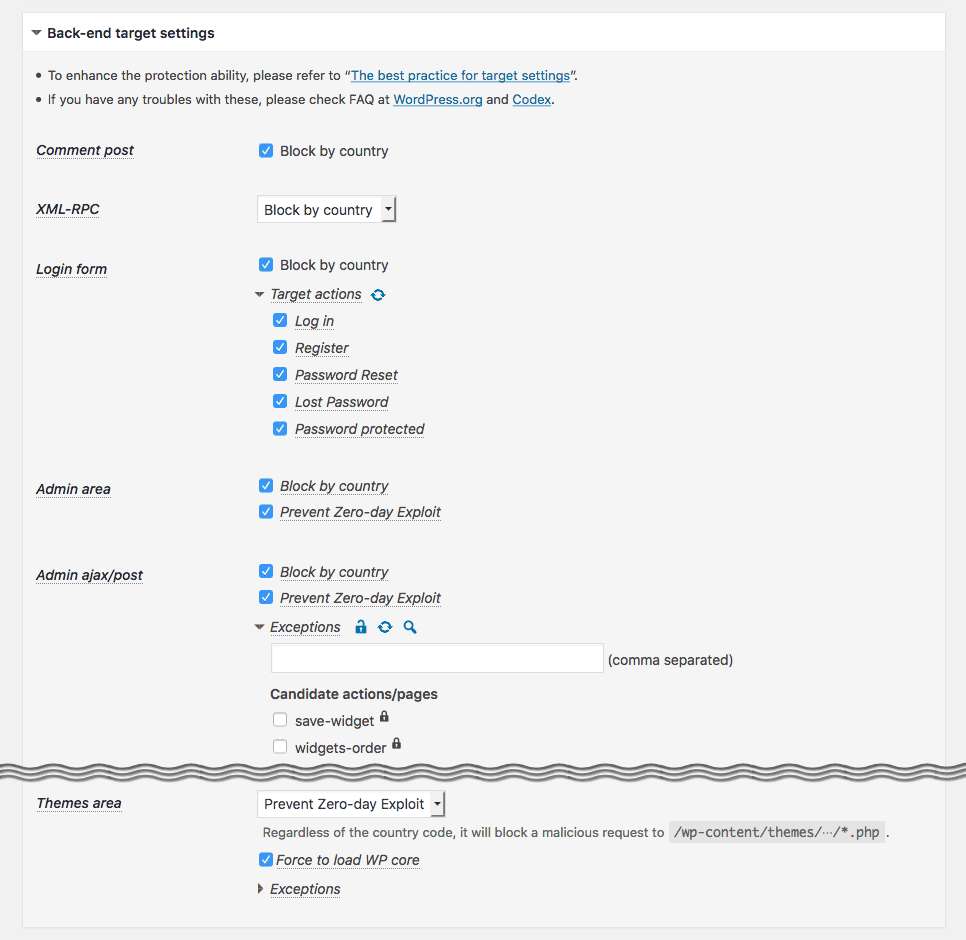
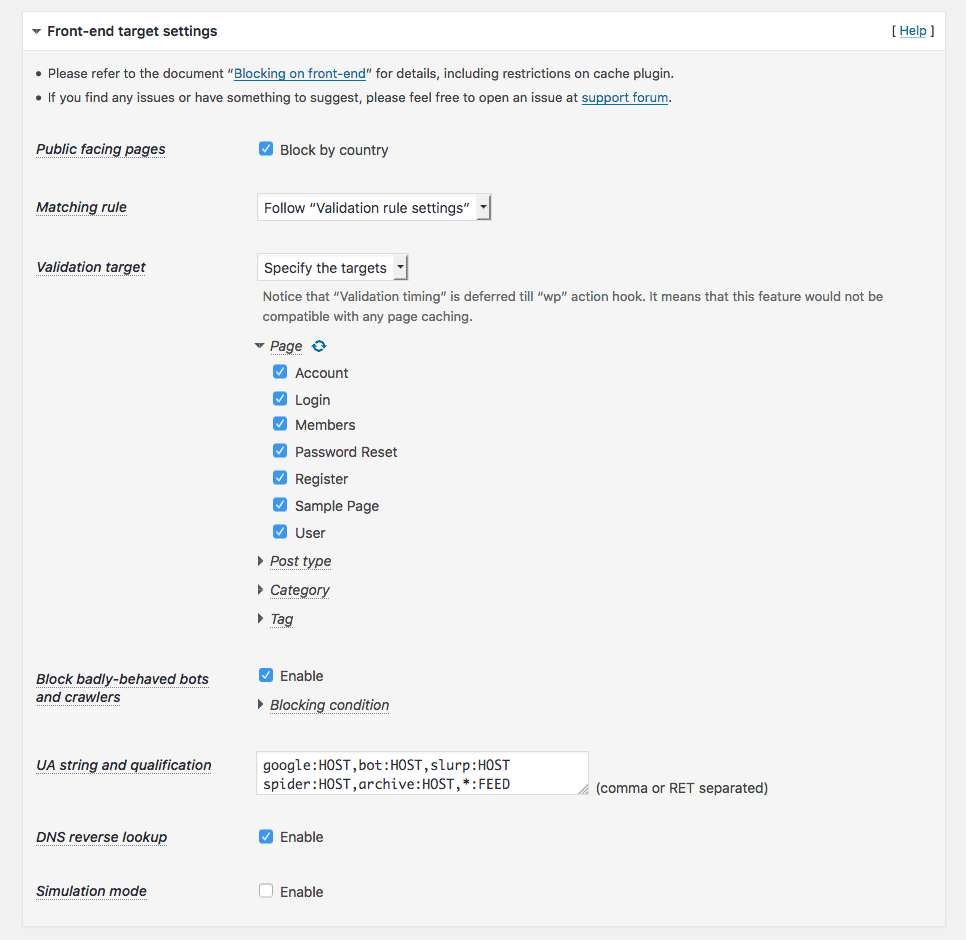
Access to the basic and important entrances into back-end such aswp-comments-post.php,xmlrpc.php,wp-login.php,wp-signup.php,wp-admin/admin.php,wp-admin/admin-ajax.php,wp-admin/admin-post.phpwill be validated by means of a country code based on IP address. It allows you to configure either whitelist or blacklist to specify the countires, CIDR notation for a range of IP addresses and AS number for a group of IP networks. -
Zero-day Exploit Prevention:
Unlike other security firewalls based on attack patterns (vectors), the original feature “WordPress Zero-day Exploit Prevention” (WP-ZEP) is focused on patterns of vulnerability. It is simple but still smart and strong enough to block any malicious accesses towp-admin/*.php,plugins/*.phpandthemes/*.phpeven from the permitted countries. It will protect your site against certain types of attack such as CSRF, LFI, SQLi, XSS and so on, even if you have some vulnerable plugins and themes in your site. -
Guard against login attempts:
In order to prevent hacking through the login form and XML-RPC by brute-force and the reverse-brute-force attacks, the number of login attempts will be limited per IP address even from the permitted countries. -
Minimize server load against brute-force attacks:
You can configure this plugin as a Must Use Plugins so that this plugin can be loaded prior to regular plugins. It can massively reduce the load on server. -
Prevent malicious down/uploading:
A malicious request such as exposingwp-config.phpor uploading malwares via vulnerable plugins/themes can be blocked. -
Block badly-behaved bots and crawlers:
A simple logic may help to reduce the number of rogue bots and crawlers scraping your site. -
Support of BuddyPress and bbPress:
You can configure this plugin so that a registered user can login as a membership from anywhere, while a request such as a new user registration, lost password, creating a new topic and subscribing comment can be blocked by country. It is suitable for BuddyPress and bbPress to help reducing spams. -
Referrer suppressor for external links:
When you click an external hyperlink on admin screens, http referrer will be eliminated to hide a footprint of your site. -
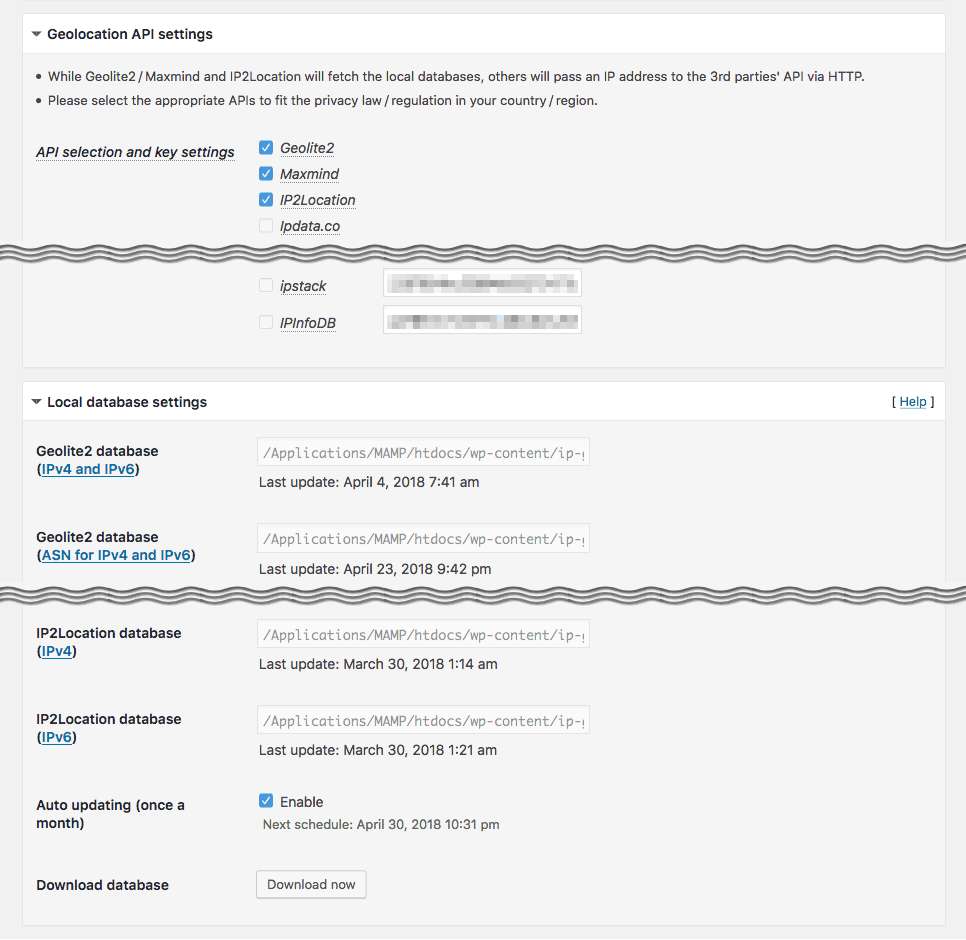
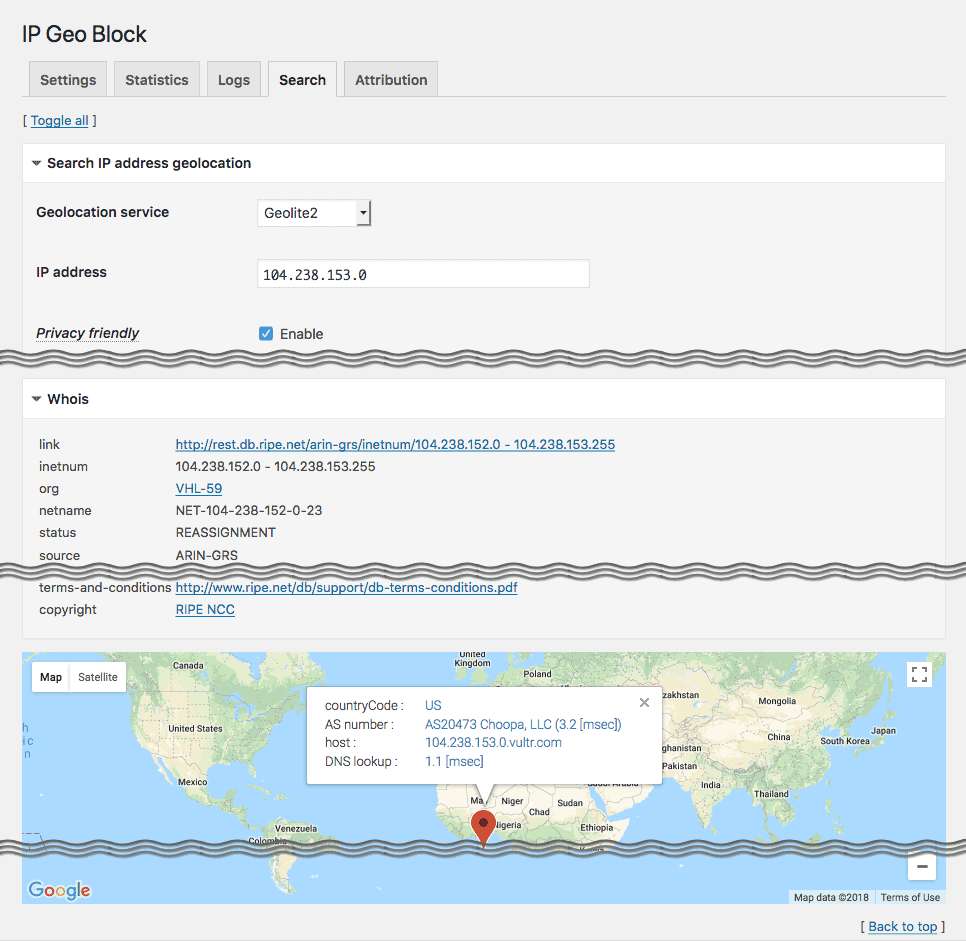
Multiple source of IP Geolocation databases:
MaxMind GeoLite2 free databases (it requires PHP 5.4.0+) and IP2Location LITE databases can be installed in this plugin. Also free Geolocation REST APIs and whois information can be available for audit purposes.
Father more, dedicated API class libraries can be installed for CloudFlare and CloudFront as a reverse proxy service. -
Customizing response:
HTTP response code can be selectable as403 Forbiddento deny access pages,404 Not Foundto hide pages or even200 OKto redirect to the top page.
You can also have a human friendly page (like404.php) in your parent/child theme template directory to fit your site design. -
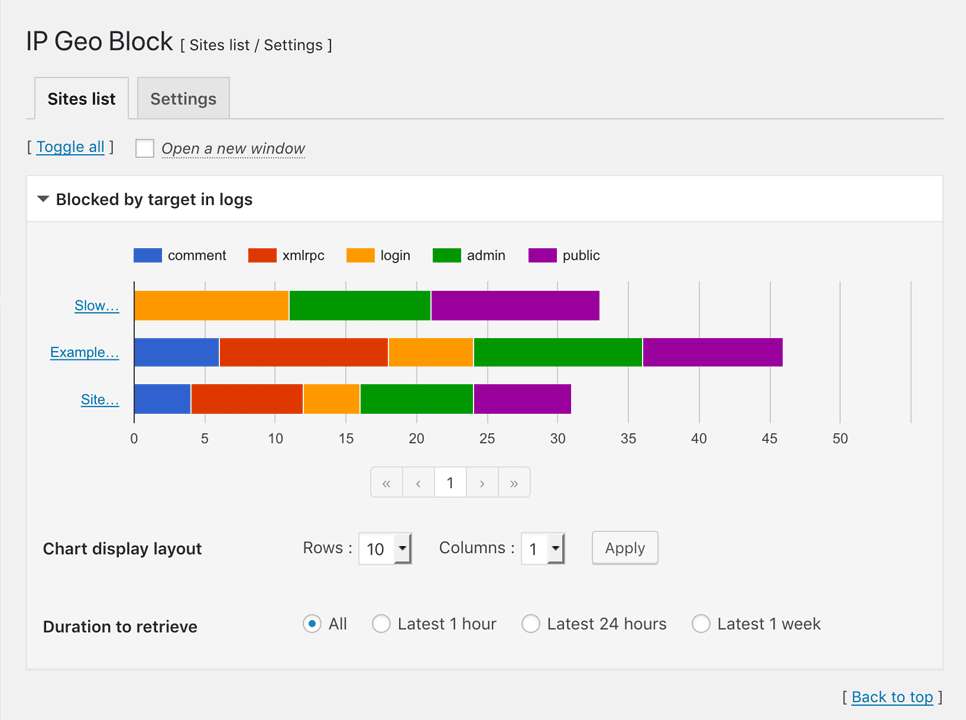
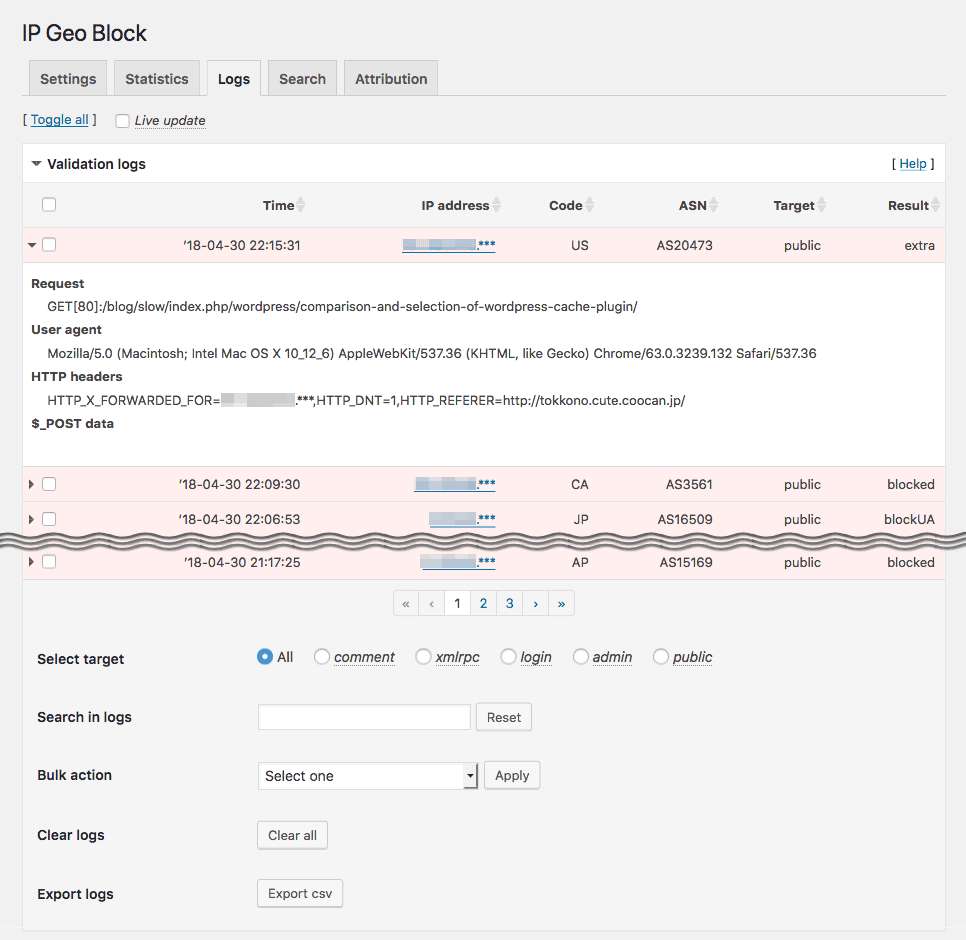
Validation logs:
Validation logs for useful information to audit attack patterns can be manageable. -
Cooperation with full spec security plugin:
This plugin is lite enough to be able to cooperate with other full spec security plugin such as Wordfence Security. See this report about page speed performance. -
Extendability:
You can customize the behavior of this plugin viaadd_filter()with pre-defined filter hook. See various use cases in samples.php bundled within this package.
You can also get the extension IP Geo Allow by Dragan. It makes admin screens strictly private with more flexible way than specifying IP addresses. -
Self blocking prevention and easy rescue:
Website owners do not prefer themselves to be blocked. This plugin prevents such a sad thing unless you force it. And futhermore, if such a situation occurs, you can rescue yourself easily. -
Clean uninstallation:
Nothing is left in your precious mySQL database after uninstallation. So you can feel free to install and activate to make a trial of this plugin’s functionality.
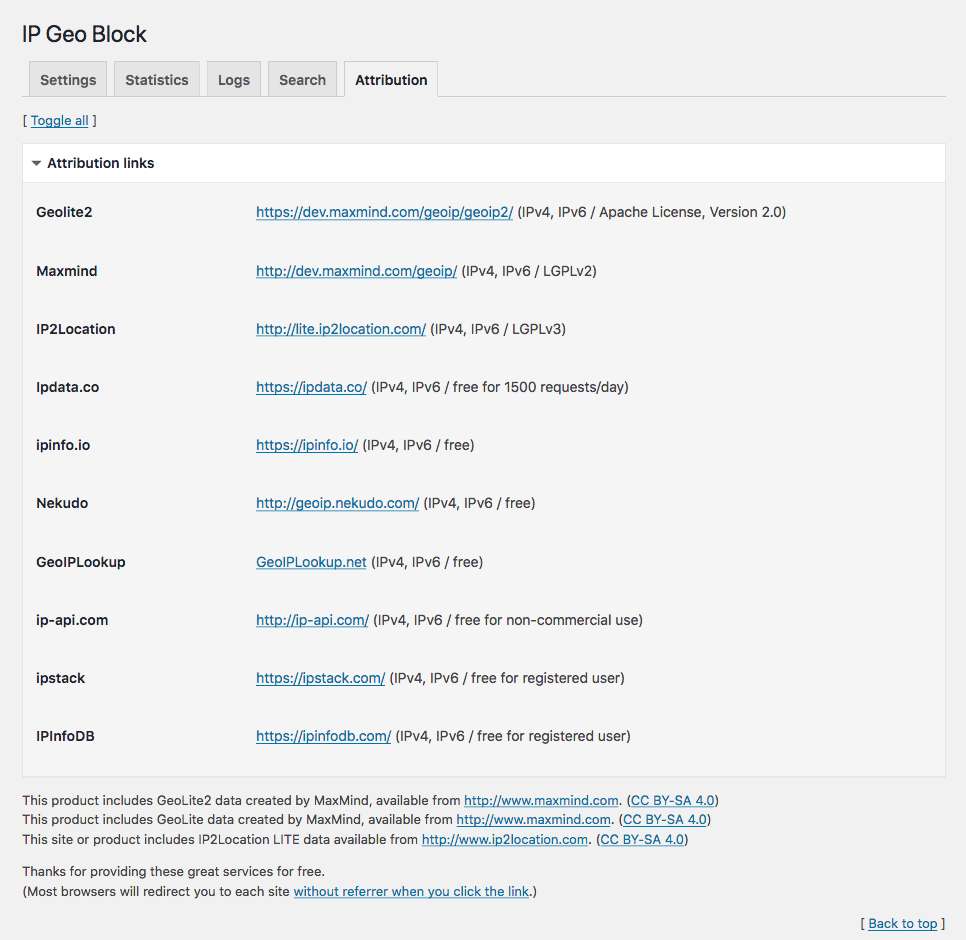
Attribution
This package includes GeoLite2 library distributed by MaxMind, available from MaxMind (it requires PHP 5.4.0+), and also includes IP2Location open source libraries available from IP2Location.
Also thanks for providing the following great services and REST APIs for free.
- http://ip-api.com/ (IPv4, IPv6 / free for non-commercial use)
- http://geoiplookup.net/ (IPv4, IPv6 / free)
- https://ipinfo.io/ (IPv4, IPv6 / free)
- [https://ipapi.com/](https://ipapi.com/ “ipapi – IP Address Lookup and Geolocation API) (IPv4, IPv6 / free, need API key)
- https://ipdata.co/ (IPv4, IPv6 / free, need API key)
- https://ipstack.com/ (IPv4, IPv6 / free for registered user, need API key)
- https://ipinfodb.com/ (IPv4, IPv6 / free for registered user, need API key)
Development
Development of this plugin is promoted at WordPress-IP-Geo-Block and class libraries to handle geo-location database are developed separately as “add-in”s at WordPress-IP-Geo-API.
All contributions will always be welcome. Or visit my development blog.
Known issues
- No image is shown after drag & drop a image in grid view at “Media Library”. For more details, please refer to this ticket at Github.
- From WordPress 4.5,
rel=nofollowhad no longer be attached to the links incomment_content. This change prevents to block “Server Side Request Forgeries” (not Cross Site but a malicious internal link in the comment field). - WordPress.com Mobile App can’t execute image uploading because of its own authentication system via XMLRPC.