Description
Faison Zutavern, Jon Valcq, and Emma Edgar, from Orion Group LLC, bring superior Brute Force Attack protection to WordPress with their new plugin, Project Force Field. By tracking failed login attempts and taking advantage of Apache’s mod_rewrite module, Project Force Field stops Brute Force Attacks from bogging down your sites and servers.
Special thanks to Chris Aykroid for the plugin banner 😀
Contributing
If you would like to contribute or fork Project Force Field, we currently have a repo on Bitbucket. You can find it here
Features!
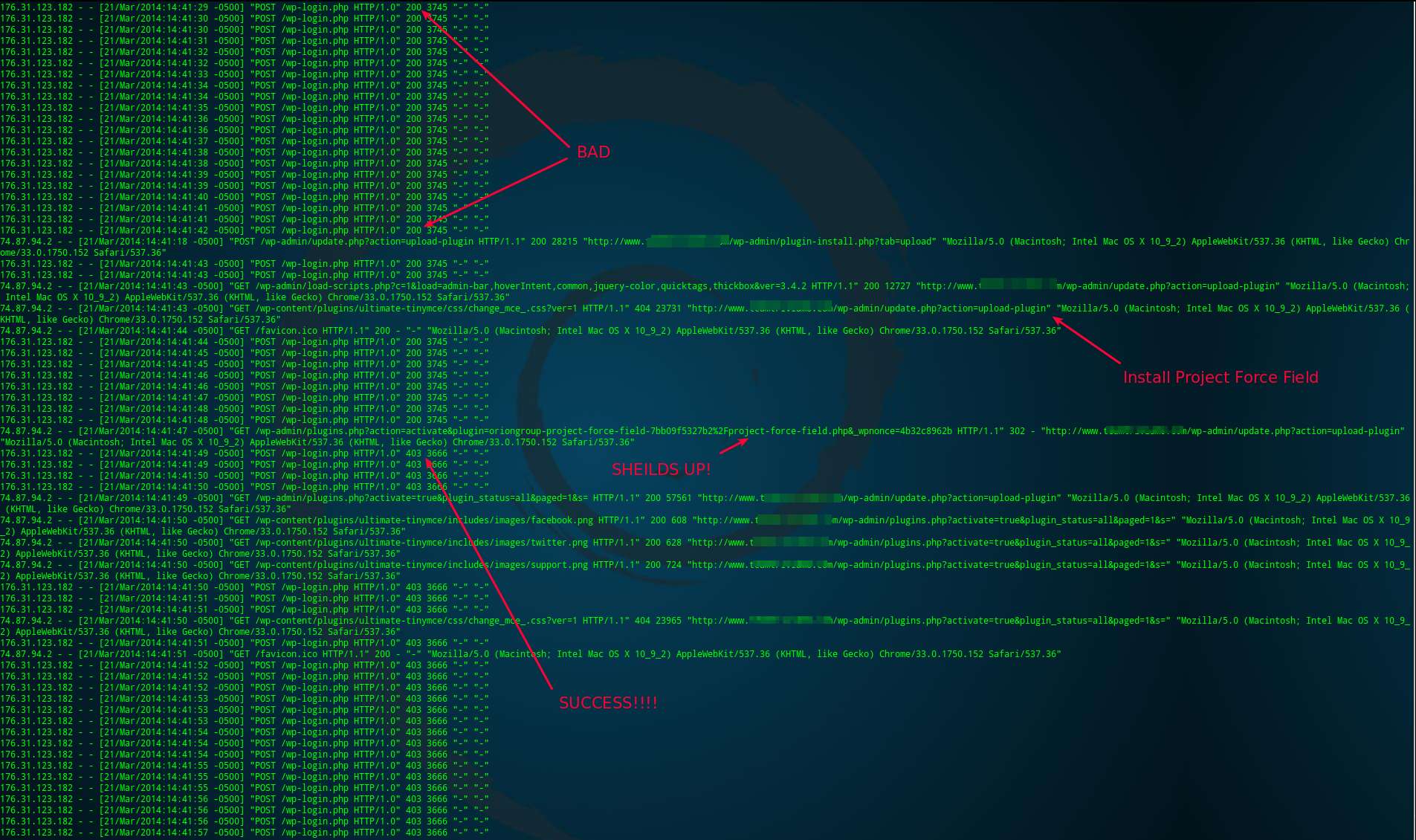
- Sends a 403 error code to anyone visiting /wp-login.php – All brute force attacks we’ve seen target /wp-login.php. By responding with a 403 error, your WordPress files aren’t loaded, the Database isn’t queried, and the attacker doesn’t figure out your password.
- Changes the default login url – While a so-called hacker is being deflected by your new Force Field, you will log in with ease at /wp-admin/. When you do that, WordPress will redirect you to the new, proper login url.
- Automatically changes the login when a Brute Force Attack is detected – When too many login failures occur within a minute, Project Force Field shifts polarity! The new login you previously used now responds with a 403 error, and a large random number is now used as your login url! After some time, the login will return back to normal.
- Unlimited polarity shifts – If a Brute Force Attacker gets smart and writes a script to check for the new login url, Project Force Field will continue to detect the attack and change the login.
- Define the login yourself – By defining
OGFF_LOGINin your wp-config.php, you can set the login to be almost anything you want. - Stops WordPress User Enumeration Exploit – Many brute force attacks use the WordPress User Enumeration exploit to easily figure out valid usernames. We stop that to protect your site, and respond with a 403 to save your server.
Future Features!
- Multisite Support – It’s not there yet, that’s pretty lame, so I’m going to fix that before anything else!
- Adjust the login failure threshold – Currently, Project Force Field assumes a brute force is underway when there have been 30 login failures within a minute. This might not be ideal for large websites, so we want to let you increase that amount to 300 if needed.
- Add optional email notification for brute force events – If you want to know when your website is under attack, we want to let you know. In a near future version, we will let you add email addresses to be notified of brute force attacks, and any other important related events that we add in the future.
- Add last resort .htaccess password lockdown – If a so-called hacker writes a script that continues to learn the new login url, Project Force Field won’t help much. In an upcoming version, we will check to see how many times the login url was changed, determine if the Brute Force Attack is smart, and lockdown the login with an .htaccess password.